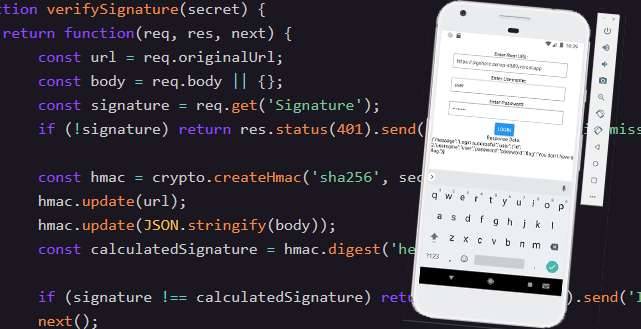
#6 Sign Here!
This Web + Mobile required reverse engineering an APK file and its React Native Hermes bytecode to find an HMAC signing key that it uses to communicate with the web server.
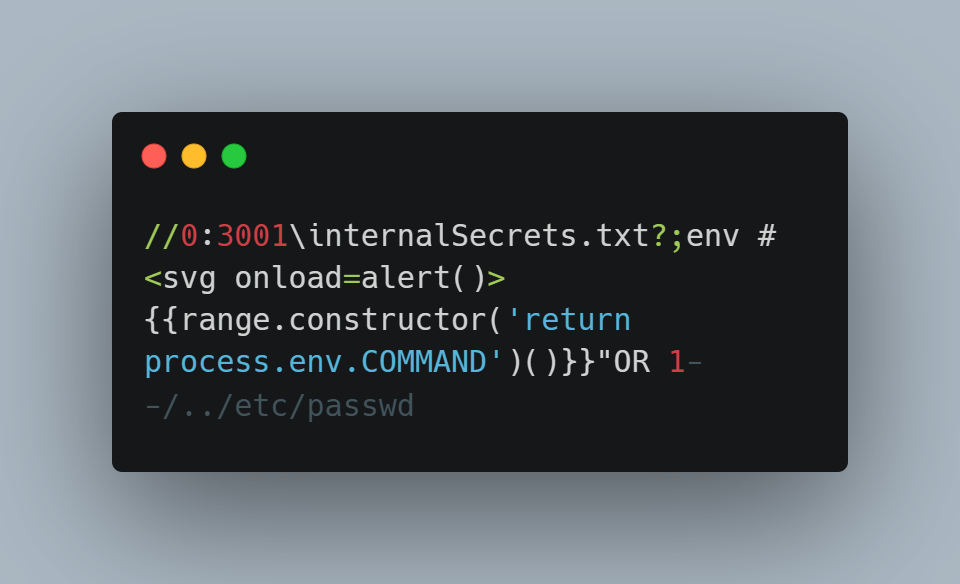
#5 Payloadception
This crazy challenge required you to write a single payload that exploits 6 vulnerabilities at the same time while being restricted to only 137 characters. We learn not only about a few simple vulnerabilities but also clever tricks to optimize their length.
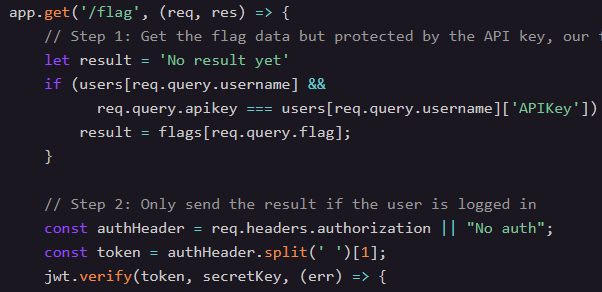
#4 Sensitive Flags
Bypass an authorization check in JavaScript in an unintended way by abusing prototype properties that exist on every object.
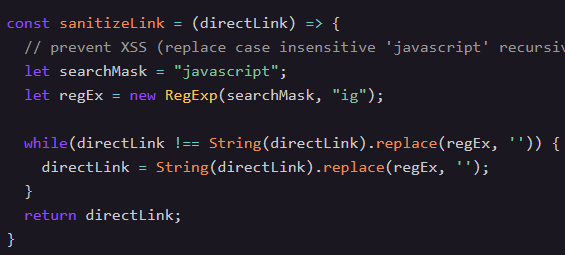
#3 Hack the Menu
Perform Cross-Site Scripting (XSS) while bypassing a "javascript" filter by inserting special characters that the browser ignores.
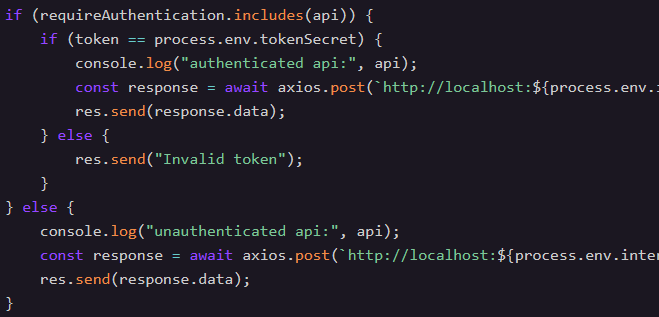
#2 Augustus Gloop's Secret
Bypass authentication on a custom proxy by confusing the check while fetching an otherwise authenticated endpoint.
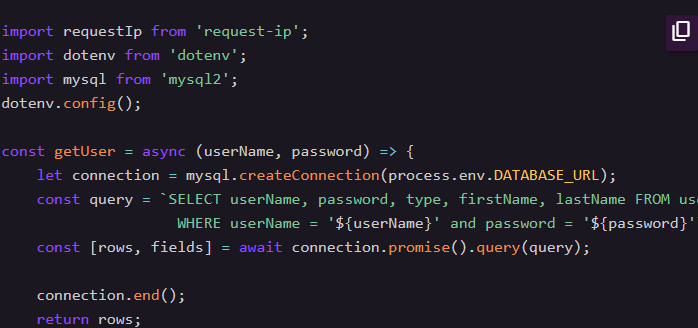
#1 Login as an Admin
Perform a SQL Injection attack using 'UNION SELECT' to leak an administrators password.