Nexus Void
This medium web challenge was an interesting chain of multiple vulnerabilities. All of them were quite easy to spot in the source code, but creating a custom deserialization gadget was a fun thing I hadn't done before. The idea of checking for credentials in compiled binaries is good advice as well as a developer might leave them in a repository by mistake.
The Challenge
We get a big ZIP file full of C# (.cs) source code for the server, as well as a remote host. From the source code inside of Nexus_Void/ there are a few different folders containing parts of the application:
Nexus_Void/
├── Controllers/
│ ├── HomeController.cs
│ └── LoginController.cs
├── Helpers/
│ ├── DatabaseContext.cs
│ ├── EncodeHelper.cs
│ ├── JWTHelper.cs
│ ├── SerializeHelper.cs
│ └── StatusCheckHelper.cs
├── Middleware/
│ └── JWTMiddleware.cs
...
└── Program.cs
The main Program.cs file defines the routes and other configurations, as well as some 'JWT Middleware':
...
// Map default (/) route to Login controller
app.;
// Use JWT middleware for paths starting with /home
app.;
app.;
In Visual Studio Code, we can Ctrl+Click on this keyword to jump to its definition. Here it references another class JWTHelper:
public
This helper class has a few methods for dealing with the JWT tokens, like generating and validating them:
public
JWT Secret Key
In the code above the _configuration["JWT:Secret"] variable is used to get the secret for generating JSON Web Tokens (JWTs). Maybe we can find the value of this variable in the code, or at least how it is generated:
);
);
);
);
"JWT:Secret" got no results apart from the code accessing it, but just "Secret" revealed a very interesting hit in Nexus_Void/obj/Release/net7.0/PubTmp/Out/appsettings.json. It seems like the regular appsettings.json was redacted, but there was still a Release build of the application that contains temporary files including the original Secret. We can confirm this secret by using the application to register an account, and logging in as a user:
Not too interesting of a website, but now our cookie "Token" has been set to a JWT the real server generated for us. Using jwt.io we can input the JWT to see its Payload with our name in it, and then add the "BRO IDK WHAT SHOULD I ADD HERE MEH FUCK IT" string we found as the key. and...
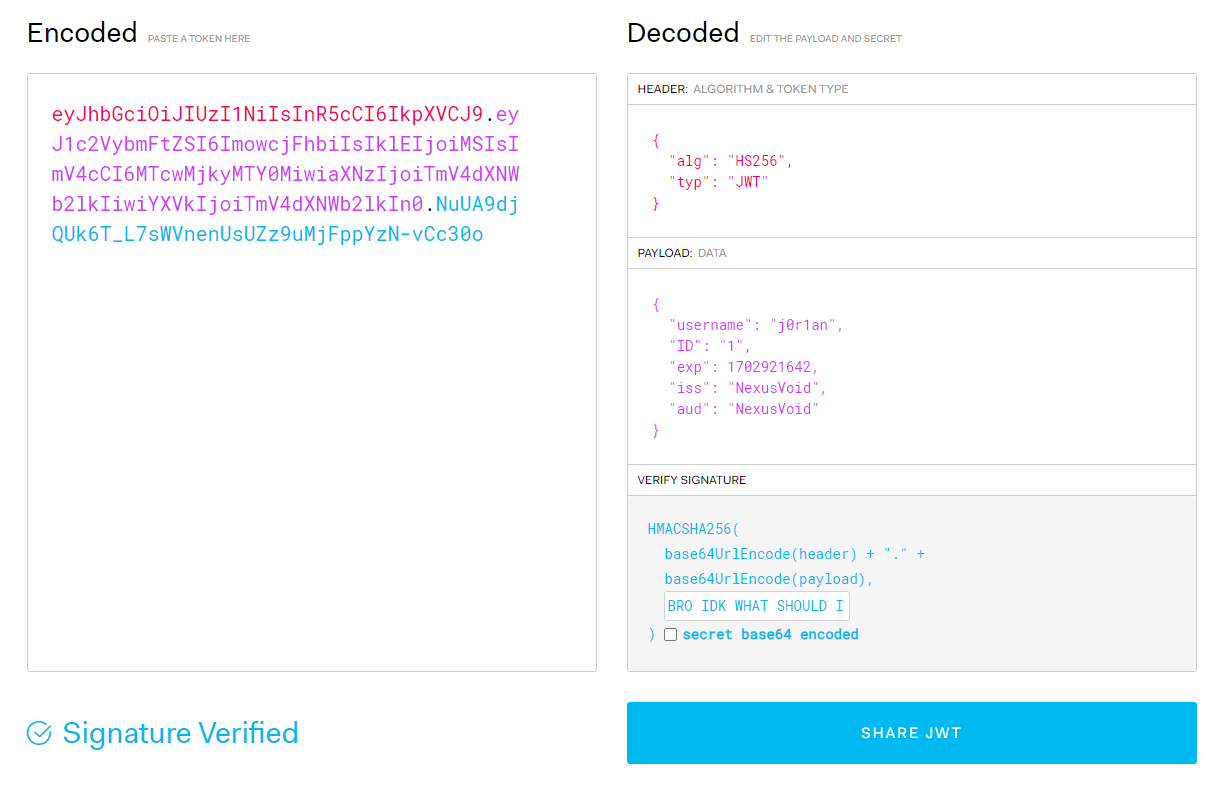
"Signature Verified"! That means the key is correct and we can forge our own tokens by changing the payload on this same page. Let's find out what damage we can do now that we control all values in the JWT payload.
SQL Injection
Starting at the HomeController.cs because we found earlier that this path uses the JWT Middleware:
public A very glaring SQL Injection vulnerability exists here in the ID variable for the Wishlist() method, which is passed directly into a templated SQL query without parameterization. The HttpContext.Items is passed from the JWT middleware as our JWT payload, so by changing the ID in our JWT, we can inject anything into this SQL statement. This can be tested if we add any items to our favorites, and then change the JWT to have a SQL Injection payload in its payload:
Token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImowcjFhbiIsIklEIjoiJyBPUiAnJz0nIiwiZXhwIjoxNzAyOTIxNjQyLCJpc3MiOiJOZXh1c1ZvaWQiLCJhdWQiOiJOZXh1c1ZvaWQifQ.PlMqpme-ibdDIpRMRzAJ9h56oQIjUF9-oOwrPeONHmA
After replacing our cookie with this value, we find that it still loads our Wishlist items, and all items on the website for that sake. Fetching items is not very useful as in this case, wishlist items are not very secret. But one more thing we can do is alter the query so it returns our arbitrary data. Using the UNION SELECT keyword it is possible to add more items to the results with our own query, which may be any string we like:
SELECT * from Wishlist WHERE ID='' UNION SELECT 1337, 'someone', 'data'
The payload will be ' UNION SELECT 1337, 'someone', 'data and will set wishlist to have id=1337, username="someone", and data="data". But how do we exploit this vulnerability?
JSON Deserialization
Right there in the same code snippet is another dangerous word: "Deserialize". The process of deserializing something is turning a regular string, sometimes with binary data, into an Object in that programming language. For C#, this will turn a string being wishlist.data into an object. These types of behaviors are very often targets for exploits as such a generic function might allow deserializing any type of object, not just one the server expects. That can lead to all kinds of issues because the source code may create custom code that executes when an object of a certain type is created, to initialize it for example. But when an attacker controls this data it can allow them to run some specific pieces of code, sometimes chaining them together to form the malicious behaviour.
In this case, we can follow it into the SerializeHelper class which uses Newtonsoft.Json to deserialize the data:
public
// EncodeHelper.cs
public
Note the TypeNameHandling = TypeNameHandling.All setting here, this explicitly tells the deserializer to allow creating any type of object, the dangerous behavior we talked about. The str is decoded using EncodeHelper.Decode which is simply a Base64 decoding function. Then it is directly unserialized and only after converted to the right List<ProductModel> type.
This means that if we can find a gadget that executes interesting code when it is constructed, we will be able to execute it at will with any object properties.
While trying to understand how to exploit this vulnerability myself, I came across the following writeup:
https://www.vaadata.com/blog/exploiting-and-preventing-insecure-deserialization-vulnerabilities/
It explains the C# case with the same deserialization case as we see. In their case, a "CommandManager" class existed that uses its own properties in a useful way to the attacker, inside the set { } method which is run when the object is constructed. Let's try to find anything similar:
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
; ;
Many classes use the set keyword, but almost all of them are empty with set;. If we search for any method that is not immediately closed, we find only one result in StatusCheckHelper.cs:
using .;
After reading the linked article, that looks very familiar! Almost the same command execution functionality exists here with a string parameter "command" that when set, runs the _command variable that comes from value as bash command, and sets the result as the output property. It is a prime example of a deserialization gadget because when we construct an object with the type of StatusCheckHelper, and set the .command property, its value will be executed as a shell command by the server. We just have to put it in the right format:
This $type value comes from the namespace and class name concatenated with a .. Then the last part is the project name which you can find in various places like the name of the .csproj file, and the root folder name. Now that we have a clear plan, we just need to put it together into one big payload that gets us the flag.
Putting everything together
Our first vulnerability was the ability to forge JSON Web Tokens, which we can do easily in Python using the PyJWT library. In this token payload, we put a SQL Injection as the "ID" value with a UNION SELECT statement. Then finally we use the Deserialization gadget, in JSON format and Base64, to execute the command that exfiltrates the flag.
Here's a script that does all this:
=
=
=
return
return
=
=
=
When we run the script, the token will be valid, our SQL injection will create the deserialization data, which is executed, sending the /flag* file to our webhook server. Then we can read the flag in the POST data!
HTB{D0tN3t_d3s3r1al1z4t10n_v14_sQL_1NJ3CT10N_1s_fun!}