MLWeb
Find an Insecure Deserialization vulnerability in a Machine Learning library to get RCE after an admin triggers your uploaded model
GCC Online
Provide any arguments to a GCC compiler to run arbitrary code at compile-time. Eventually, bypass a ban list filter to pass dangerous options
frenzy flask
This directory traversal challenge has two solutions, one to read the flag and another resulting in RCE that can bypass more filters.
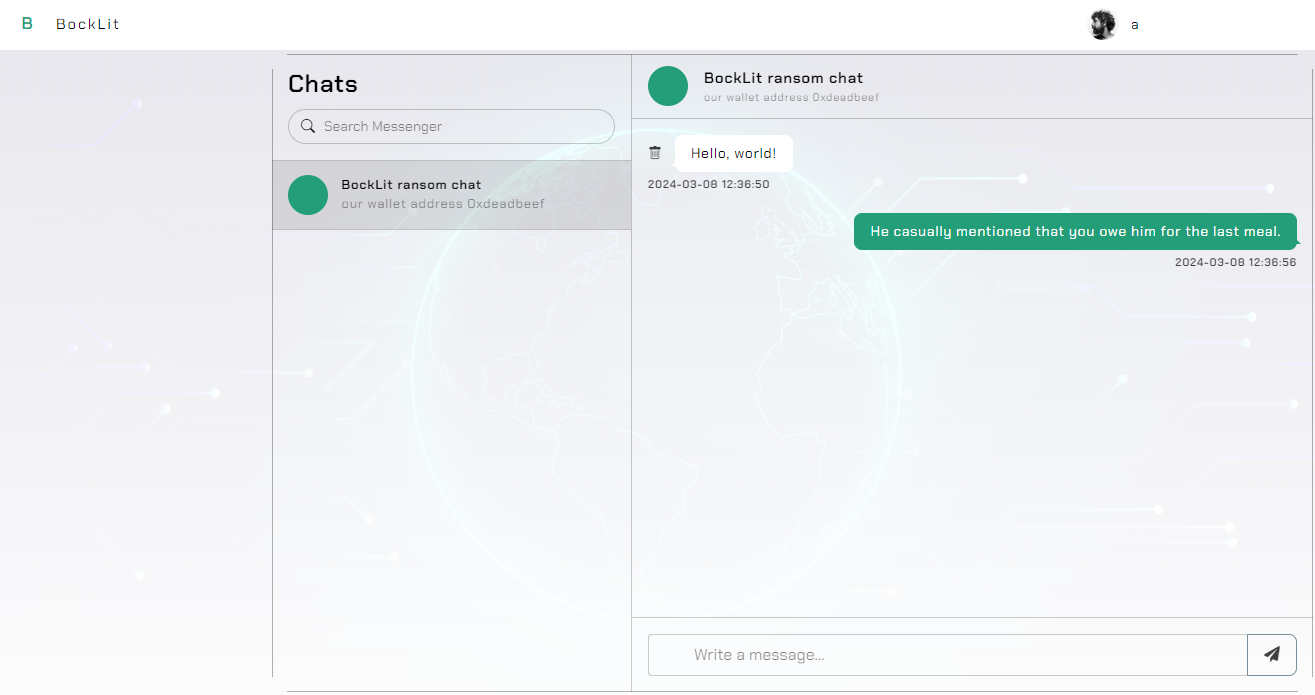
Genie Pwn Adventure (+ Revenge)
A dashboard representing LockBit's chat function with an administrator bot. This one was solved in a completely unintended way that did not involve a bot at all, just logic!
SuperAES
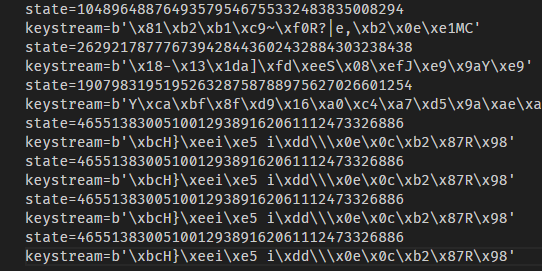
A cryptography challenge involving a combination of a flawed Linear Congruential Generator (LCG) and a custom AES mode. Recover part of the plaintext to leak the repeated flag from a repeating keystream.
Bad Habit
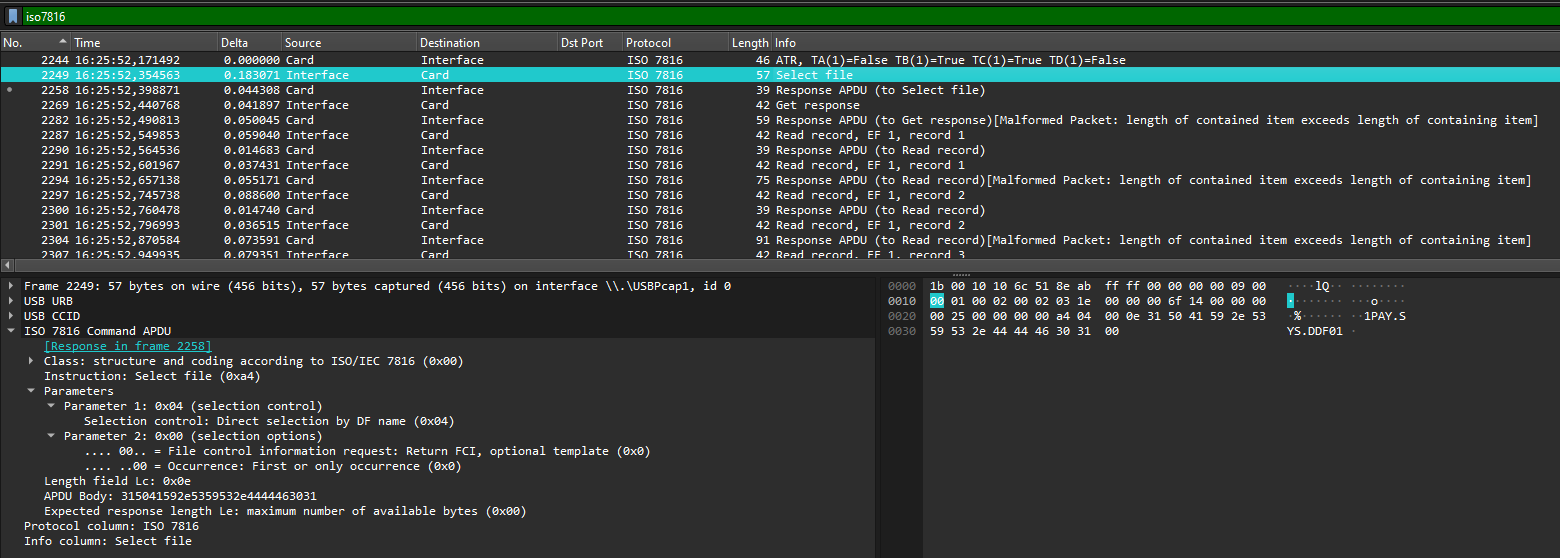
Reverse engineer a smart card protocol in Wireshark to recover the card number and expiry date from a USB capture